Seems Legit: This Phishing Email, 5 Million Gmails Exposed, and Preventing Email Hack
Over a week or so, the online world was shaken by leaks of celebrity photos.
Today, in tech world, on the spotlight is the report of “about 5 million Gmail accounts and passwords leaked online.” According to the said reports, the Gmail information were posted on a Russian Bitcoin forum BTCsec by a certain user named “tvskit”.
Google responded quickly through a blog post stating, “We found that less than 2% of the username and password combinations might have worked and our automated anti-hijacking systems would have blocked many of those login attempts.”
Google emphasized that the leak didn’t originate internally but likely through “other old sources” that hackers collected from over time such as through small hacking sites or malwares on computers.
I posted about this recent “hacking incident” on Facebook and a friend confirmed that his account was exposed. Fortunately, what the dump contained was his old password.
Still a serious issue, you might want to change your password now just to be sure even if you’re confident that your information wasn’t exposed. Aside from using complex passwords, it is also highly recommended to change passwords from time to time.
But how do these hackers obtain email account information?
There are many ways that this is done. Some do it by getting information from hack sites since most people use username and password combination across various sites and platforms.
Others infect computers with malware that can sniff information from your PC and give them unauthorized access to it.
Another common way that hackers do it is through phishing.
Wikipedia defines phishing as an “attempt to acquire sensitive information such as usernames, passwords, and credit card details (and sometimes, indirectly, money) by masquerading as a trustworthy entity in an electronic communication.”
Just this morning, a friend from Facebook posted a copy of an email she recently received via Yahoo! Mail.
This is a perfect example of a phishing email. Actually, if you just glanced at it, you might actually fall for it. She even captioned it as, “…one of the most realistic phishing emails I’ve seen.”
Seeing the email, I actually thought so too, that it “seemed legit.”
Unlike most phishing emails I have seen in the past, this one almost didn’t show any red flag. Other phishing emails are easy to determine because of grammatical errors, informal choice of fonts, or suspicious sender.
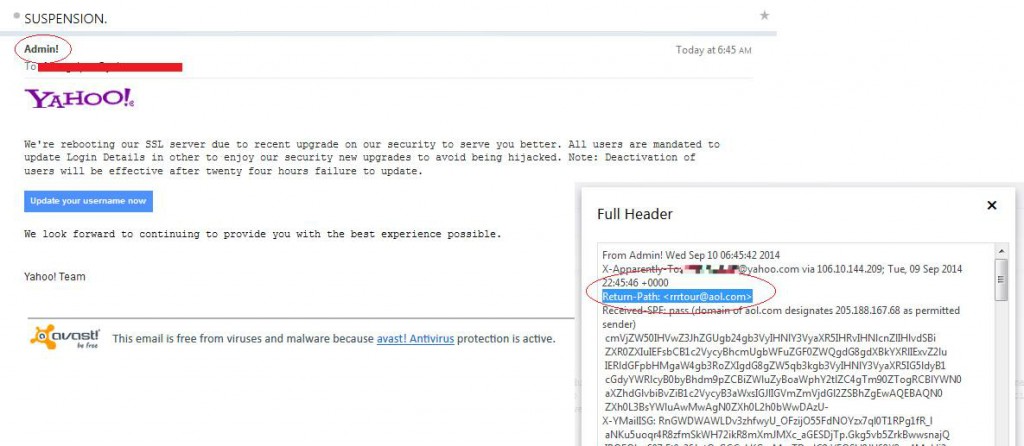
If we take a look at this specific email in greater detail, there is a red flag noted by the original poster.
The sender is from “Admin!”
It’s quite weird to receive a formal message from a team like Yahoo! and have an exclamation point (!) after the sender’s name. It’s actually phishy. If you view the headers (on the right of the image), you’ll see that the return path is from an email address “rrrtour@aol.com” and not Yahoo!.
Another red flag, which may not be very apparent, is that the title in bold face had a period (.). Titles don’t have periods period.
These simple mistakes should derive suspicion but if we are quick to judge, which we often are most of the time, then we are extremely vulnerable to this.
So, what can happen when you fall for a phishing email such as this one?
If you fall trap for this, definitely you will click the “Update your username now” button. Then, you will actually update your username information, in all honesty and very accurately (because who wants a suspended account, right?). Then, this information will be redirected to the real sender, which was masked by the Admin! sender. Eventually, they can use this information to obtain access to your email account, or if there are other accounts that you might expose to them, to those too.
Of course the title is alarming. Seeing that the title says, “SUSPENSION.”, you will want to take action to avoid this from happening, especially if you use your email frequently and for business purposes.
What my friend did is a good move. She said, “…so I tweeted Yahoo and asked if this is indeed legit; It’s not. They pointed out that the sender used the old Yahoo logo.”
She added, “I also checked the return-path (or sender-address) and it points to an AOL account. The message intends to affright the reader. If di ka pa nagkakape mapapaclick ka talaga! (Rough translation: If you haven’t had coffee yet, you’ll definitely click it!) :))”
What can you do when you receive a phishing email?
1. You can do what she did. Most service providers are extremely active on Twitter. You can quickly obtain responses from that microblogging site.
2. If you don’t have a Twitter account, you can check for red flags if you are a bit suspicious of a certain email. If it checks certain boxes, it probably is phishing.
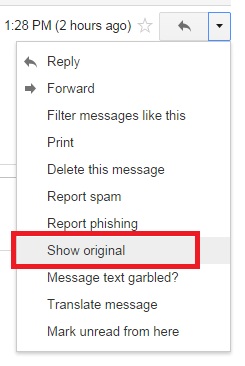
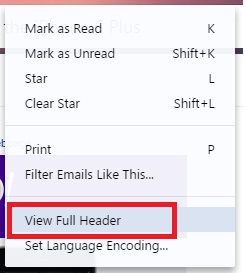
3. You can also check the headers to see if there are certain information that are masked. This might require some tech skills but the important information to check is the return path. This will let you see if it’s a genuine address or not. See images below to learn how to do this on Gmail or Yahoo!.
Bottom line is, if it arises suspicion on your side, NEVER provide personal information.
And again, if you can change your passwords from time to time, that will make you “less susceptible” to hacking.
Have you checked if your Gmail account was compromised on the recent hacking exposure?
There are several ways to check here.
Have other tips to check for phishing and prevent email hack?
Share it in the comments.
Seems Legit: This Phishing Email, 5 Million Gmails Exposed, and Preventing Email Hack